39 advanced antivirus techniques in network security
Advanced Threat Protection & Detection - Trend Micro Advanced sandbox analysis. Deep Discovery Analyzer provides custom sandbox analysis to extend the value of security products, such as endpoint protection, web and email gateways, network security, and other Deep Discovery offerings. Suspicious objects or URLs are automatically or manually sent for analysis, and threat insight is automatically shared with Trend Micro and third-party products. What is Network Security: Its Types and Management - Software Testing Help Security management in any network, whether public or private, is a set of policies and routine procedures implemented by the networking system to shield the network from unauthorized access, denial of computer service, interruption in running, etc is known as Network Security Management. It also emphasizes on round the clock monitoring of the ...
10 Malware Detection Techniques Used by AntiVirus. How ... - PCInsider Here are the 10 Malware Detection Techniques used by Antivirus/Antimalware software to detect Viruses, Worms, Adware, Spyware, Ransomware, Trojan Horse, and all the remaining types of Malware. File Signature Analysis Heuristic Analysis Behavioural Analysis Cloud Analysis (and File Rating) Sandbox Analysis (Virtualization)
Advanced antivirus techniques in network security
Advanced Network Security (CS4155) - Cyber Threat Intelligence In CS4155 Advanced Network Security, students get in addition to the theory also the opportunity for studying vulnerabilities and countermeasures in networking systems and communication protocols in detail, including in-depth study of protocol security analysis as well as a handson implementation of defense mechanisms on actual systems. Advanced Threat and Network Analysis: Your Security Secret Weapon Today, blocking the latest exploits requires a combination of advanced threat and network protection techniques that help you predict and influence outcomes, not merely react. Learn more about the specific technologies being used to prevent, detect and eliminate advanced threats at ESET's next webinar. Topics include: Top Network Security Service Providers 2022 | Channel Insider It enables MSPs to prevent cyberattacks by scanning authorization issues, security implementation, and antivirus status. Key Differentiators Enhance managed services and increase recurring revenue by automating IT management, offering comprehensive patch management, and full security vulnerability scanning
Advanced antivirus techniques in network security. PDF CTS 2317 Advanced Network Security - Miami Dade College 4. Describing the security capabilities of information systems, including memory protection, Trusted Platform Module (TPM), encryption and decryption. 5. Describing methods to assess and mitigate the vulnerabilities of security architectures, designs, and solution elements, including: client-based and server-based systems, databases, (PDF) Communications and Multimedia Security. Advanced Communications and Multimedia Security. Advanced Techniques for Network and Data Protection Lecture Notes in Computer Science - Germany doi 10.1007/b13863 Full Text Open PDF Abstract Available in full text Categories Computer Science Theoretical Computer Science Date January 1, 2003 Authors Unknown Publisher Springer Berlin Heidelberg PDF Advanced Cyber Security Techniques - CEMCA Title Advanced Cyber Security Techniques Advisors Mr. R. Thyagarajan, Head, Admn. & Finance and Acting Director, CEMCA Dr. Manas Ranjan Panigrahi, Program Officer (Education), CEMCA Prof. Durgesh Pant, Director-SCS&IT, UOU Editor Mr. Manish Koranga, Senior Consultant, Wipro Technologies, Bangalore Authors How to Protect Networks against Advanced Evasion Techniques(AET) Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic.
Five Ways to Defend Against Network Security Threats Antivirus software can detect and prevent malicious files from being installed on a system, and it should be updated regularly to include the latest definitions. 2. Create strong passwords. Another essential step in protecting a network is to create strong passwords. advanced evasion technique (AET) - SearchSecurity Network Security Threat management advanced evasion technique (AET) Definition advanced evasion technique (AET) By TechTarget Contributor An advanced evasion technique (AET) is a type of network attack that combines several different known evasion methods to create a new technique that's delivered over several layers of the network simultaneously. PDF Advanced Network Security - kkohls.org Advanced Network Security Lecture 8: Attacks and Mobile Networks Harald Vranken, Katharina Kohls ... ciphering and integrity protection (RRC) and transport of IP packets. I RLC: Transport PDCP data in ... Attack Techniques I Machine learning: Make sense of metadata I Deep learning: Automatic feature generation ADVANCED CYBERSECURITY TECHNOLOGIES: HOW IT WORKS | Kaspersky True cybersecurity should be based on the synergy of various protection techniques, from classic AV records to behavior-based detection with deep learning models. ... KATA applies machine-learning models, sandbox and other advanced techniques to detect the most complex threats. ... Cloud threat intel: Kaspersky Security Network (KSN)
How to Protect Network Against Advanced Malware | securitywing By using Garter's 5 styles of advanced defence framework, you can apply the following five defence mechanism in your network: Traffic Analysis Under normal circumstances, your network follows a specific traffic pattern which you can easily recognize when you analyse your traffic for a month or so. Advanced Approaches to ATM Network Protection - Security Intelligence An Advanced Approach to ATM Security Security specialists who choose an advanced protection strategy should address all threat types using a security information and event management (SIEM)... Advanced Threat Prevention - Palo Alto Networks Safeguard your organization with industry-first preventions. Building on the industry-leading Threat Prevention security service, Advanced Threat Prevention protects your network by providing multiple layers of prevention during each phase of an attack while leveraging deep learning and machine learning models to block evasive and unknown C2 completely inline. Network Antivirus | Sophos Advanced Security with XDR, MTR Intercept X Advanced with MTR Advanced. Foundational techniques ... See why Sophos is the industry leader in network antivirus security. Our claims are backed with nearly 35 years of experience protecting 500,000 businesses around the world. Sophos is the industry's most comprehensive network protection built to stop the widest range of threats.
Improve Network Security with Advanced Threat Protection Find malicious content traversing the network via hardware emulation and supervised machine learning models Filter large amounts of network data and events via a correlation engine to eliminate false positives and zero in on a smaller set of real intrusions These features provide several benefits for network administrators.
Gartner: 'Five Styles of Advanced Threat Defense' can protect ... In short, Gartner's "Five Styles" of defense are: Style 1 - Use Network Traffic Analysis techniques to establish baselines of normal traffic patterns, (for example anomalous DNS traffic ...
Top Advanced Threat Protection Solutions & Software 2022 - TechRepublic whether incorporated within endpoint protection agents or assisting in the form of a hardware appliance or email or firewall filter, advanced threat protection technologies assist network...
Advanced Network Security Technologies | Cato Networks Anti-malware engines use both signature and heuristic-based techniques to identify and block malware within a network. Intelligent anti-malware engines are an important safeguard against zero-day threats or modifications of malware designed to avoid detection based on signature alone. Intrusion Prevention System (IPS)
Advanced Approaches for Information Security and Protection • Network Security • WLAN Security • Jammer Detection • Interference Avoidance • Beamforming • Cryptography • Digital Watermarking • IoT Security • Multiplexing techniques Extended versions of papers submitted to the above-mentioned workshop can also be considered in this Research Topic.
Network Analytics: From Detection to Active Prevention Cynet Network Analytics protection spans the wide range of advanced attacks stages, utilizing network visibility, behavioral analysis, deterministic modules and threat intelligence. You can enable Cynet built-in preventions or tailor a customized flow utilizing host isolation, traffic block and user disable.
Advanced Threat Protection: A Real-Time Threat Killer Machine - Cynet Advanced threat protection (ATP) is a set of practices and solutions that you can use to detect and prevent advanced malware or attacks. Generally, ATP solutions include a combination of network devices, malware protection systems, email gateways, endpoint agents, and a centralized management dashboard.
What Is Network Security | Network Security Solutions | EC-Council This skill-based, 50% lab-intensive network security program takes students through the depths of network security tools and techniques. Other benefits of the program include: Mapped to NICE 2.0 Framework Accredited by ANSI, NICF, GCHQ, DoD etc. Comprehensive Learning Exam Based on Practical Challenges
Network Security Basics- Definition, Threats, and Solutions The Importance of Network Security. Network security is vital to maintaining the integrity of your data and the privacy of your organization and employees. It encompasses everything from the most basic practices, such creating strong passwords and fully logging out of community computers, to the most complex, high-level processes that keep networks, devices and their users safe.
Inside out: Get to know the advanced technologies at the core of ... Behavior-based ML engine - Suspicious behavior sequences and advanced attack techniques are monitored on the client as triggers to analyze the process tree behavior using real-time cloud ML models. Monitored attack techniques span the attack chain, from exploits, elevation, and persistence all the way through to lateral movement and exfiltration.
Protection Methods for Network Security - GeeksforGeeks Network security means some measures taken to protect computer networking from unauthorized access and risks. Some protection methods are used to reduce security issues. Authentication : Authentication is the process of recognizing or identifying a user's identity whether it is true, real, or not.
Top Network Security Service Providers 2022 | Channel Insider It enables MSPs to prevent cyberattacks by scanning authorization issues, security implementation, and antivirus status. Key Differentiators Enhance managed services and increase recurring revenue by automating IT management, offering comprehensive patch management, and full security vulnerability scanning
Advanced Threat and Network Analysis: Your Security Secret Weapon Today, blocking the latest exploits requires a combination of advanced threat and network protection techniques that help you predict and influence outcomes, not merely react. Learn more about the specific technologies being used to prevent, detect and eliminate advanced threats at ESET's next webinar. Topics include:
Advanced Network Security (CS4155) - Cyber Threat Intelligence In CS4155 Advanced Network Security, students get in addition to the theory also the opportunity for studying vulnerabilities and countermeasures in networking systems and communication protocols in detail, including in-depth study of protocol security analysis as well as a handson implementation of defense mechanisms on actual systems.















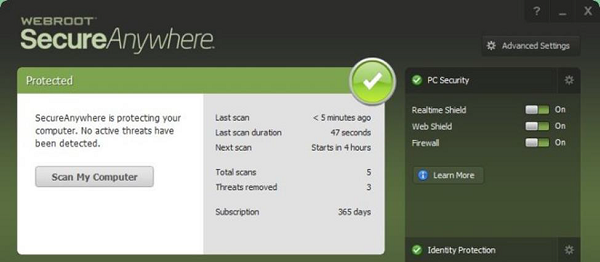







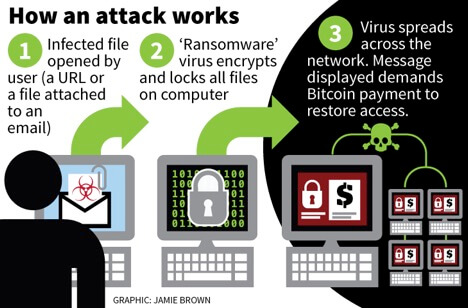
0 Response to "39 advanced antivirus techniques in network security"
Post a Comment